DORA Regulation: Latest Commission Delegated Regulations
The Digital Operational Resilience Act (DORA) enhances cybersecurity and operational resilience for EU financial entities. It sets standards for managing ICT-related incidents, enforcing risk management, and regulating third-party providers.

Introduction to DORA Regulation
The Digital Operational Resilience Act (DORA) represents a critical advancement in the European Union's regulatory landscape, specifically designed to enhance the cybersecurity and operational resilience of financial entities. As the financial sector becomes increasingly reliant on digital technologies, the need for robust frameworks to manage ICT-related incidents and cyber threats has never been more pressing. DORA addresses these challenges by ensuring that financial institutions are not only prepared to handle such incidents but also possess the necessary strategies and tools to mitigate risks and maintain operational continuity.
Source
[1]

[2]

Objectives and Scope of DORA Regulation
DORA aims to create a cohesive and comprehensive approach to digital operational resilience across the European Union. The regulation targets a broad spectrum of financial entities, including banks, insurance companies, investment firms, and payment service providers. Its primary objectives include:
- Enhancing Cybersecurity: By setting stringent standards for identifying, managing, and reporting cyber threats and ICT-related incidents, DORA seeks to fortify the cybersecurity infrastructure of financial institutions.
- Ensuring Operational Continuity: DORA mandates the implementation of robust business continuity plans and disaster recovery strategies to ensure that critical financial services remain uninterrupted in the face of ICT disruptions.
- Strengthening Risk Management: The regulation emphasizes the need for comprehensive ICT risk management frameworks that include regular assessments, monitoring, and reporting of potential risks.
- Regulating Third-Party Providers: Recognizing the significant role of third-party ICT service providers, DORA establishes rigorous guidelines for managing third-party risks, including contractual obligations and performance monitoring.

Key Provisions of DORA Regulation
On June 25, 2024, the European Union took a significant step forward in operationalising DORA by publishing three pivotal Commission Delegated Regulations in the Official Journal of the EU (OJ). These regulations are designed to provide detailed technical standards and guidelines crucial for the effective implementation of DORA. They come into force twenty days after their publication, marking a new era of digital resilience for financial entities within the EU.
Technical Aspects and Implementation
The Commission Delegated Regulations supplement the core DORA framework with specific, actionable requirements that financial entities must adhere to. These include:
- Incident Classification and Reporting: Detailed criteria for classifying ICT-related incidents and cyber threats, along with mandatory reporting thresholds, ensure a standardized approach across all financial entities. This uniformity aids in the timely identification and management of potential threats.
- Risk Management Tools and Methods: The regulations stipulate the use of advanced tools and methodologies for assessing and managing ICT risks. This includes continuous monitoring, threat detection, and the implementation of preventive measures.
- Governance and Accountability: Financial entities are required to establish clear governance structures and assign specific responsibilities for ICT risk management. Regular audits and reviews ensure that these structures are effective and up-to-date.
- Third-Party Risk Management: Detailed guidelines for managing risks associated with third-party ICT service providers include due diligence processes, contractual requirements, and ongoing performance evaluations. These measures help mitigate risks stemming from external dependencies.
DORA Regulation: Commission Delegated Regulation (EU) 2024/1772
Supplementing Regulation (EU) 2022/2554 with regard to regulatory technical standards specifying the criteria for the classification of ICT-related incidents and cyber threats, setting out materiality thresholds, and specifying the details of reports of major incidents.
This regulation forms a critical component of the DORA Regulation by providing detailed technical standards essential for the classification and reporting of ICT-related incidents and cyber threats. These standards aim to harmonize practices across financial entities, ensuring a unified approach to incident management and reporting.
Key Provisions:
Classification of ICT-Related Incidents
The regulation establishes comprehensive criteria for classifying ICT-related incidents and cyber threats. This classification system is vital for maintaining consistent and harmonised reporting across all financial entities under the DORA Regulation. The criteria for classification include:
- Impact on Clients and Counterparts: The number of clients and financial counterparts affected by the incident.
- Transaction Metrics: The number and amount of transactions impacted by the incident.
- Reputational Impact: The potential damage to the financial entity’s reputation as a result of the incident.
These criteria ensure that incidents are categorized based on their severity and impact, allowing for more effective management and response strategies.
Materiality Thresholds
The regulation defines clear materiality thresholds to determine the significance of ICT-related incidents. These thresholds ensure that only incidents with substantial impact are reported, thus reducing unnecessary administrative burdens on financial entities. The materiality thresholds are based on:
- Service Downtime: The duration of service interruptions caused by the incident.
- Geographical Spread: The extent to which the incident affects different geographical regions.
- Data Losses: The amount and sensitivity of data lost or compromised during the incident.
- Economic Impact: The financial losses incurred as a result of the incident.
By setting these thresholds, the regulation ensures that reporting is focused on incidents that genuinely affect the operational integrity and resilience of financial entities.
Reporting Requirements
The regulation specifies detailed reporting requirements for major ICT-related incidents. These requirements include:
- Comprehensive Documentation: Financial entities must provide detailed accounts of the incidents, including the nature of the incident, its impact, and the steps taken in response.
- Timely Submission: Reports must be submitted promptly to the competent authorities to facilitate swift supervisory actions and mitigate further risks.
- Relevant Details: Emphasizes capturing all pertinent details to support supervisory functions and prevent the spread of issues across the financial sector.

Digital Operational Resilience Act: Commission Delegated Regulation (EU) 2024/1773
Supplementing Regulation (EU) 2022/2554 with regard to regulatory technical standards specifying the detailed content of the policy regarding contractual arrangements on the use of ICT services supporting critical or important functions provided by ICT third-party service providers.
This regulation underscores the importance of robust contractual arrangements and risk management practices concerning third-party ICT service providers, which are crucial for the operational resilience of financial entities.
Contractual Arrangements
The regulation mandates specific content for policies related to contracts with third-party ICT service providers. These requirements ensure that all critical aspects of ICT services are covered, including:
- Service Level Agreements (SLAs): Detailed agreements that outline the expected level of service, performance metrics, and remedies for non-compliance.
- Data Protection Measures: Ensuring that data handled by third-party providers is secure and complies with relevant data protection regulations.
- Contingency Plans: Strategies for maintaining operations and recovering services in case of disruptions.
Risk Management
The regulation highlights the necessity for rigorous risk assessment and management practices concerning third-party ICT services. This includes:
- Proactive Risk Identification: Continuously identifying and assessing potential risks associated with third-party services.
- Risk Mitigation Strategies: Implementing measures to mitigate identified risks, ensuring that third-party services do not compromise operational resilience.
Policy Requirements
Detailed guidelines are provided on the content of policies to ensure comprehensive coverage of contractual obligations and risk management strategies. This includes:
- Continuous Monitoring: Regularly monitoring the performance and compliance of third-party providers with contractual terms.
- Incident Response: Ensuring that policies include robust incident response procedures.
- Regulatory Compliance: Policies must ensure that all third-party services comply with relevant regulatory standards.
Governance Arrangements
The regulation mandates annual reviews and updates of policies by the management body to ensure timely implementation of changes. Key aspects include:
- Clear Responsibilities: Establishing clear internal responsibilities for managing, controlling, and documenting contractual arrangements.
- Governance Structures: Creating governance structures that support effective oversight and management of third-party risks.
Due Diligence
A comprehensive due diligence process is required for selecting and assessing prospective ICT third-party service providers. This process ensures:
- Resource Assessment: Providers have the necessary resources, expertise, and standards to deliver ICT services reliably.
- Risk Mitigation: Thorough evaluation of potential risks associated with third-party services.
Monitoring and Audits
The regulation requires ongoing monitoring of third-party performance and adherence to ICT security standards. This includes:
- Performance Reviews: Regular audits and independent reviews to assess compliance and performance.
- Security Standards: Ensuring third-party services meet established security standards and protocols.
Exit Strategies and Termination
The regulation specifies requirements for documented exit plans, periodic reviews, and testing. This ensures:
- Seamless Transitions: Smooth transitions in case of service interruptions or termination of third-party services.
- Continuity Plans: Ensuring continuity of critical services during transitions.
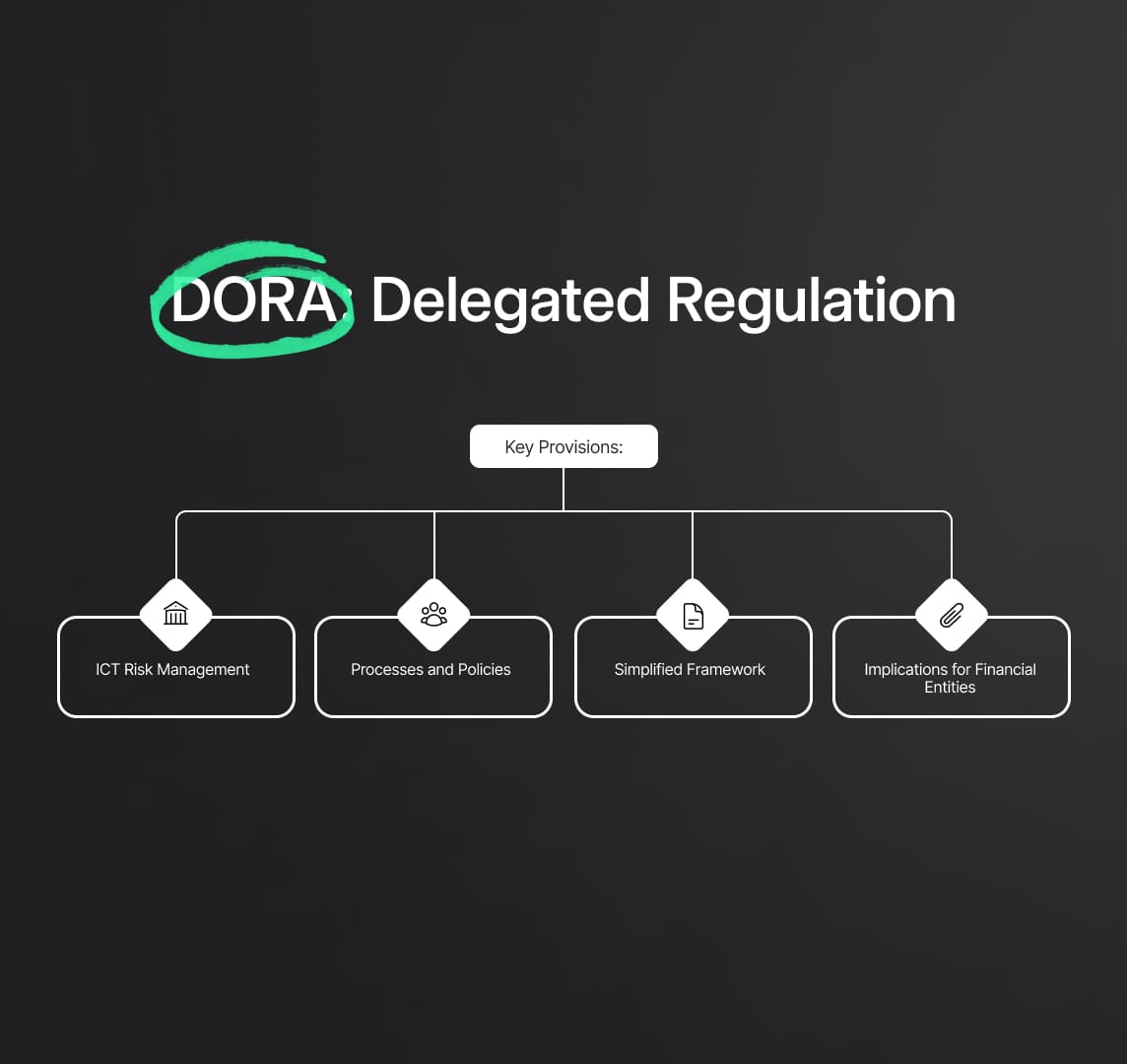
DORA: Delegated Regulation (EU) 2024/1774
Title: Supplementing Regulation (EU) 2022/2554 with regard to regulatory technical standards specifying ICT risk management tools, methods, processes, and policies and the simplified ICT risk management framework.
This regulation under the DORA framework is critical for ensuring that financial entities implement robust ICT risk management practices. It provides detailed technical standards for ICT risk management tools, methodologies, and policies, tailored to meet the diverse needs of financial institutions.
Key Provisions:
ICT Risk Management Tools and Methods
The regulation outlines comprehensive tools and methodologies that financial entities should employ to effectively identify, assess, and manage ICT risks. These include:
- Risk Identification Tools:
- Automated Risk Scanning: Utilizing advanced software to detect vulnerabilities in ICT systems in real-time.
- Threat Intelligence Platforms: Leveraging external and internal data sources to identify potential cyber threats and emerging risks.
- Risk Assessment Frameworks:
- Quantitative Risk Assessment Models: These models use statistical methods to estimate the potential impact and likelihood of ICT risks.
- Qualitative Risk Assessment Techniques: Employing expert judgment and scenario analysis to evaluate ICT risk exposures.
- Risk Mitigation Strategies:
- Incident Response Tools: Tools designed for rapid identification, containment, and eradication of threats.
- Preventive Controls: Implementing firewalls, intrusion detection systems, and regular software updates to mitigate identified risks.
Processes and Policies
The regulation specifies detailed processes and policies required for effective ICT risk management. These are essential for establishing a structured approach to risk management within financial entities.
- Continuous Monitoring:
- Real-Time Monitoring Systems: Implementing systems that continuously monitor network activity to detect anomalies and potential security breaches.
- Regular Security Audits: Conducting periodic audits to ensure compliance with security policies and identify areas for improvement.
- Incident Detection and Response:
- Security Information and Event Management (SIEM) Systems: These systems aggregate and analyze log data from various sources to detect and respond to security incidents in real-time.
- Incident Response Teams: Establishing dedicated teams trained to respond to ICT incidents swiftly and effectively.
- Governance and Accountability:
- Defined Roles and Responsibilities: Clearly outlining the roles and responsibilities of staff involved in ICT risk management.
- Policy Documentation: Maintaining comprehensive documentation of ICT risk management policies and procedures, ensuring they are accessible and up-to-date.
Simplified Framework
The regulation also introduces a simplified ICT risk management framework tailored for smaller entities. This framework ensures that all financial institutions, regardless of size, can comply with DORA requirements without undue burden.
- Proportionality Principle:
- Tailored Risk Management: Adapting ICT risk management practices to fit the scale and complexity of the entity's operations.
- Resource Allocation: Ensuring that smaller entities can allocate resources efficiently to manage ICT risks without overextending their capabilities.
- Scalable Solutions:
- Modular Risk Management Tools: Implementing scalable tools that can grow with the entity’s needs.
- Outsourcing Options: Smaller entities may leverage external service providers for certain aspects of ICT risk management, such as threat monitoring and incident response.
- Compliance and Flexibility:
- Simplified Reporting Requirements: Streamlined reporting processes that reduce administrative burden while maintaining regulatory compliance.
- Flexible Policy Implementation: Allowing smaller entities to implement policies in a manner that aligns with their operational capabilities and resources.
Implications for Financial Entities
The implementation of the Commission Delegated Regulations under the DORA Regulation carries profound implications for financial entities within the EU. These regulations are designed to significantly enhance the operational resilience and cybersecurity of financial institutions, ensuring they are well-prepared to tackle the evolving landscape of ICT-related risks and cyber threats.
Enhanced Cybersecurity
One of the primary goals of the DORA Regulation is to establish clear and stringent standards for incident classification, reporting, and risk management. By doing so, it aims to enhance the overall cybersecurity posture of financial entities, making them more resilient to cyber threats and ICT-related disruptions. Key aspects include:
- Incident Classification and Reporting:
- Financial entities must classify ICT-related incidents and cyber threats based on standardized criteria. This includes assessing the impact on clients and financial counterparts, the number of transactions affected, and potential reputational damage.
- Detailed reporting requirements ensure that significant incidents are documented comprehensively and submitted promptly to competent authorities. This facilitates swift supervisory actions and helps prevent the spread of issues across the financial sector.
- Risk Management:
- The regulation mandates the use of advanced tools and methodologies for identifying, assessing, and managing ICT risks. This includes continuous monitoring, threat detection, and the implementation of preventive measures.
- Regular security audits and real-time monitoring systems are essential components of this approach, ensuring that financial entities can detect and respond to incidents effectively.
Risk Management
The DORA Regulation emphasises the need for comprehensive ICT risk management frameworks. These frameworks should be tailored to the specific needs and risk profiles of financial entities, allowing them to manage ICT risks more effectively. Key components include:
- Risk Assessment Frameworks:
- Financial entities are required to implement both quantitative and qualitative risk assessment techniques. Quantitative models use statistical methods to estimate potential impacts and likelihoods of ICT risks, while qualitative techniques involve expert judgment and scenario analysis.
- These assessments help identify vulnerabilities and potential points of failure within ICT systems, enabling entities to implement targeted risk mitigation strategies.
- Risk Mitigation Strategies:
- Preventive controls, such as firewalls, intrusion detection systems, and regular software updates, are crucial for mitigating identified risks.
- Incident response tools and dedicated response teams ensure that financial entities can address threats swiftly and minimise their impact.
Greater Accountability
The DORA Regulation imposes detailed requirements for contractual arrangements with third-party ICT service providers. This fosters greater accountability and transparency in outsourcing critical functions, ensuring a secure and reliable ICT ecosystem. Key elements include:
- Contractual Arrangements:
- Contracts with third-party ICT service providers must include comprehensive service level agreements (SLAs), data protection measures, and contingency plans.
- These contracts ensure that third-party providers meet the same stringent standards as the financial entities themselves, reducing the risk of disruptions and vulnerabilities.
- Due Diligence and Monitoring:
- Financial entities must conduct thorough due diligence when selecting and assessing third-party providers. This includes evaluating their resources, expertise, and compliance with regulatory standards.
- Ongoing monitoring and regular audits are essential to ensure that third-party services continue to meet contractual obligations and security standards.

DORA Compliance Obligations
To comply with the DORA Regulation, financial entities must review and update their policies and procedures. This necessitates thorough assessments of current practices and potential enhancements to meet regulatory standards. Key steps include:
- Policy Documentation:
- Financial entities must maintain comprehensive documentation of their ICT risk management policies and procedures. This ensures that all staff are aware of their roles and responsibilities and that policies are consistently applied.
- Regular reviews and updates of these policies are required to reflect changes in the regulatory environment and emerging threats.
- Training and Awareness:
- Continuous training and awareness programs are essential to ensure that all employees understand the importance of ICT security and their role in maintaining it.
- Financial entities should conduct regular drills and simulations to prepare staff for potential ICT incidents and ensure a swift and coordinated response.
Reduce your
compliance risks


