GRC Operational Risk Management
Operational Risk Management (ORM) is the process of identifying and mitigating risks to an organization's operations. It focuses on internal and external factors that can disrupt business operations and aims to protect the organization by eliminating or minimizing risk.

Why Operational Risk Management Matters?
Operational Risk Management (ORM) is the systematic process of identifying, evaluating, controlling, and monitoring risks that arise from people, processes, technology, or external events. Unlike credit or market risk—which are primarily financial—operational risk extends to the very core of how day-to-day business is conducted. Errors in internal workflows, weaknesses in IT systems, non-compliance with regulations, or failures of critical third-party vendors can each pose existential threats to organizational stability and reputation. In a Governance, Risk, and Compliance (GRC) framework, ORM is pivotal to ensuring that operational processes not only meet regulatory demands but also align with strategic objectives.
From a compliance officer’s perspective, failing to control operational risk can lead to severe outcomes:
- Reputational Damage: News of data breaches or operational failures often undermines public trust.
- Financial Penalties: Many regulations (e.g., Basel III in finance, GDPR in data protection) impose costly fines for non-compliance.
- Operational Disruption: An unanticipated system outage or supply chain failure can halt critical operations, resulting in revenue loss and eroding customer loyalty.
2. Defining Operational Risk in GRC Contexts
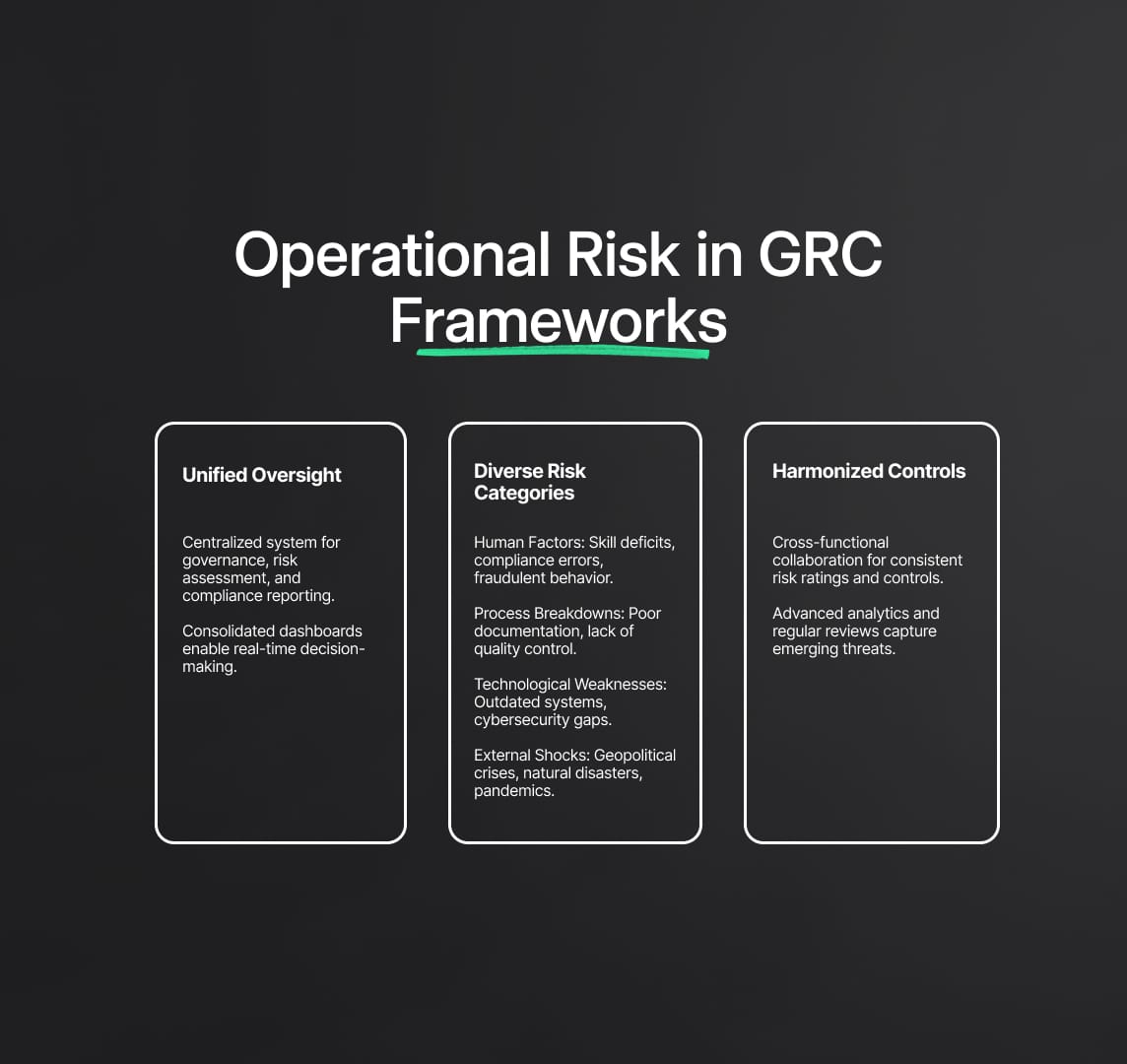
Operational risk in GRC integrates multiple dimensions of risk oversight into a unified system of governance, risk assessment, and compliance reporting. Rather than isolating operational vulnerabilities within separate units—such as IT security, HR processes, or vendor management—a GRC framework ensures that all operational exposures funnel into a single oversight mechanism. This centralized approach enables consistent risk ratings, uniform control mechanisms, and consolidated dashboards for real-time decision-making.
Yet, the variety of operational risks makes them inherently more complex to manage than solely financial or strategic categories. Examples include:
- Human Factors: Skill deficits, fraudulent behavior, compliance errors, or managerial oversight failures.
- Process Breakdowns: Inadequate documentation, unclear escalation paths, or lack of quality control in manufacturing.
- Technological Weaknesses: Legacy system vulnerabilities, data center power outages, or insufficient cybersecurity measures.
- External Shocks: Geopolitical crises, severe natural disasters, pandemic-driven workforce challenges, or partner insolvencies.
Because operational risk is so broad, a GRC framework must harmonize controls across diverse areas. This requires cross-functional collaboration, advanced analytics, and a constant review cycle to capture emerging threats.
3. Regulatory Landscape and Compliance Expectations
Many global and sector-specific regulations mandate rigorous operational risk controls:
- Basel Accords (Basel II/III)
In the banking sector, institutions must allocate capital reserves proportional to their operational risk exposure. This often necessitates advanced measurement approaches (AMA), scenario analyses, and formal risk quantification frameworks. - GDPR (General Data Protection Regulation)
Organizations handling EU residents’ personal data are obligated to secure against data leaks or unauthorized processing. Operational lapses in data handling can incur significant penalties under GDPR’s tiered fine structure. - HIPAA (Health Insurance Portability and Accountability Act)
Healthcare providers in the U.S. must ensure patient data security and privacy. Lapses in operational controls—such as insufficient access management—can lead to breaches, hefty fines, and potential loss of accreditation. - SOX (Sarbanes-Oxley Act)
Publicly traded U.S. companies must demonstrate robust internal controls to ensure accurate financial reporting, a requirement that intrinsically aligns with managing operational risk. Failure can lead to legal sanctions and reputational fallout.
For compliance officers, maintaining alignment with these rules involves:
- Documenting controls that mitigate operational risk and mapping them to relevant standards.
- Regularly testing controls to prove continuous effectiveness to regulators and external auditors.
- Reporting any material operational incidents to oversight bodies and ensuring remediation steps are transparent and traceable.
4. Core Elements of an Advanced ORM Program
4.1 Risk Identification and Taxonomy
A comprehensive risk taxonomy offers clarity on the variety of operational exposures. Categorizing risks under headings such as “Human Error,” “Process Failure,” “IT & Cybersecurity,” and “External Events” is a starting point. Deeper, sub-level classification (e.g., “payment processing errors,” “vendor SLA breaches,” “phishing attacks,” or “natural disasters”) helps track cause-effect relationships and ensures no aspect of daily operations remains overlooked.
Common Methods for Risk Identification
- Interviews and Workshops: Engage process owners and frontline employees to uncover hidden pain points.
- Incident Analysis: Examine past near-misses or operational disruptions to detect systemic control deficiencies.
- Process Mapping: Visual flow diagrams help visualize each step in a workflow and pinpoint where failures might occur.
- External Risk Databases: Industry consortia such as ORX (Operational Riskdata eXchange) in banking compile collective incident data to guide scenario modeling.
4.2 Risk Assessment and Scoring
Once identified, risks must be measured in terms of likelihood, potential impact, and velocity. In some organizations, a simple red-yellow-green heat map suffices for high-level ranking. Others implement sophisticated scoring that factors in financial loss estimates, time to detect or recover, and potential regulatory consequences.
- Qualitative Assessments: Subject matter experts assign ratings (low, medium, high) based on domain experience.
- Quantitative Models: Monte Carlo simulations, Poisson/lognormal severity modeling, and Value at Risk (VaR) estimations for operational events.
- Hybrid Approaches: Combine data-driven estimates with expert judgment for better precision, especially in scenarios lacking extensive historical data.
4.3 Control Selection and Implementation
Selecting the right mix of controls—preventive, detective, corrective—is pivotal. Preventive controls, such as multi-factor authentication or mandatory dual approvals, aim to stop events before they happen. Detective controls, like real-time monitoring dashboards or transaction anomaly detection, spot issues as they occur. Corrective controls then restore normal operations (e.g., automated failovers, incident response playbooks). For large, regulated entities, each control is often mapped to applicable standards or laws. This mapping simplifies both internal auditing and external regulatory examinations.

5. Integrating ORM into a GRC Framework
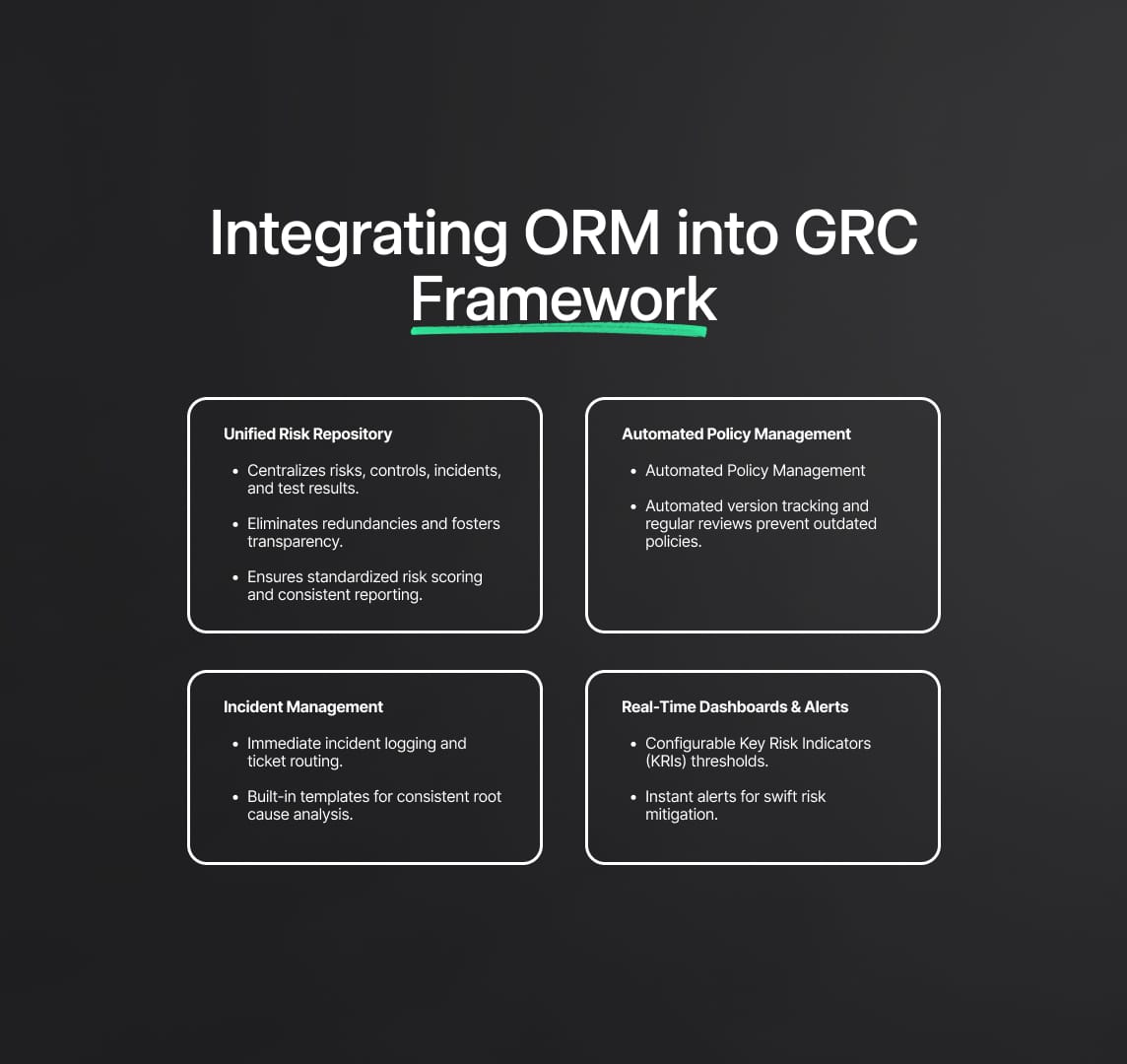
5.1 Unified Risk Repository
Centralizing operational risks, along with associated controls, incidents, and test results, within a GRC tool fosters transparency and eliminates redundant data silos. It also helps standardize risk scoring scales and ensures consistent reporting.
5.2 Automated Policy and Procedure Management
Under a GRC umbrella, policy distribution and attestation—where employees confirm they understand and commit to following key guidelines—become systematic. Regular review cycles and automated version tracking reduce the danger of outdated policies.
5.3 Incident Management
When operational lapses do occur, GRC platforms allow immediate logging of details and routing of incident tickets to relevant parties. Automated root cause analysis workflows may incorporate built-in templates, ensuring consistent data capture.
5.4 Real-Time Dashboards and Alerts
Executives and compliance officers need timely insights for critical operational concerns. By configuring thresholds in Key Risk Indicators (KRIs), the GRC system can issue real-time alerts whenever risk levels exceed predefined tolerances, enabling swift mitigation efforts.
6. The Role of Compliance Officers in Operational Risk
A compliance officer bridges the technical and regulatory aspects of ORM, ensuring that all operational controls meet both internal and external standards. Key responsibilities often include:
- Regulatory Mapping: Tracking laws (e.g., Basel III, GDPR) and mapping each requirement to specific operational controls or processes.
- Policy Enforcement: Overseeing that processes for data protection, business continuity, and employee conduct are documented and enacted enterprise-wide.
- Training and Awareness: Conducting workshops or modules that teach employees how to use operational risk management tools and report near-misses or anomalies responsibly.
- Incident Reporting: Acting as a central point for disclosures to regulators when material operational incidents occur, making sure details are accurate, timely, and reflect a culture of transparency.
Through these functions, compliance officers assure that operational risk remains a board-level priority and not just an IT or departmental concern.
7. Data-Driven Monitoring: KRIs, RCSAs, and Beyond
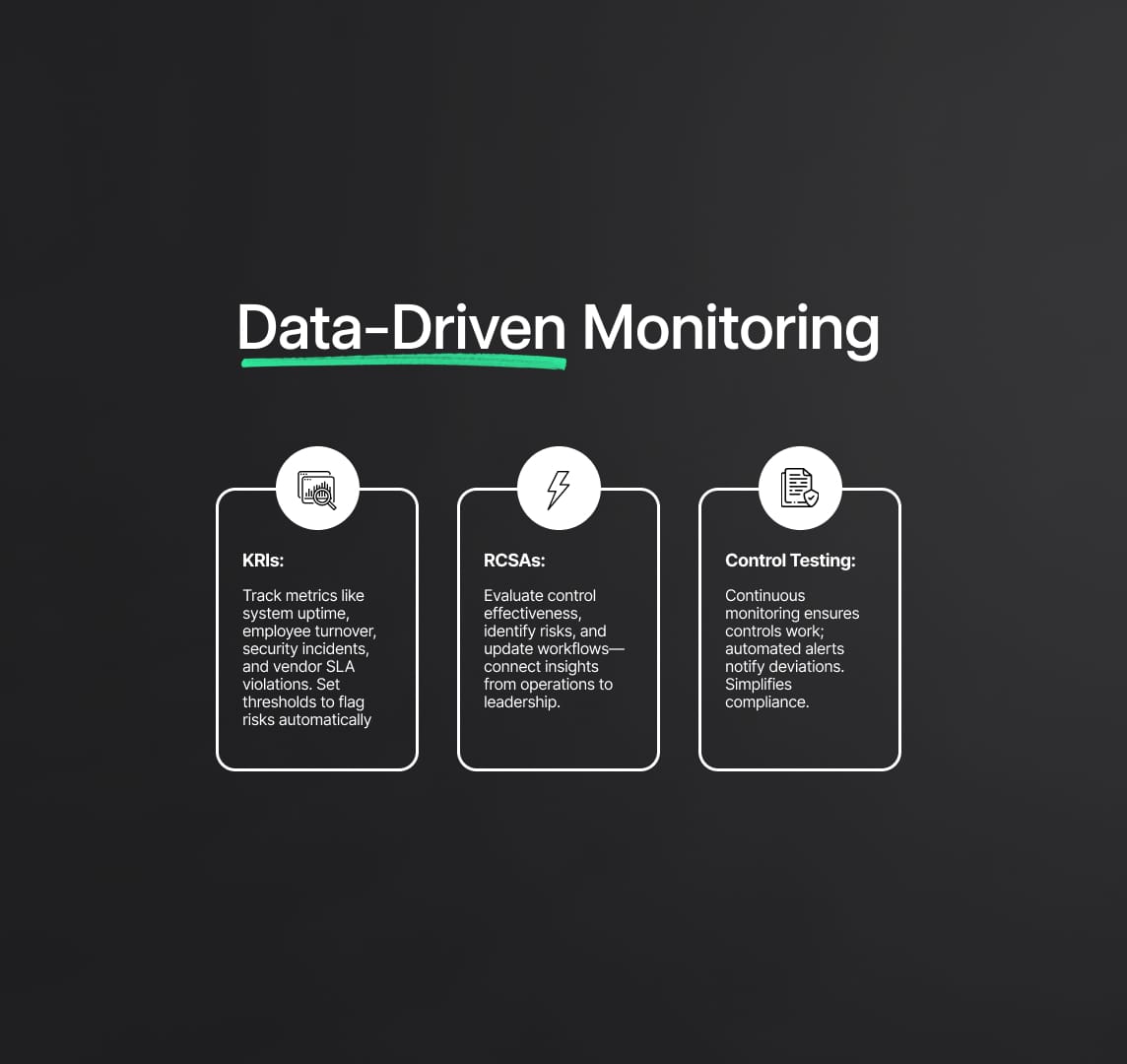
7.1 Key Risk Indicators (KRIs)
KRIs are metrics that provide early signals of heightened operational exposures. While the exact set of KRIs differs by industry, they typically include:
- System Uptime Metrics: Monitoring the availability of mission-critical software and infrastructure.
- Employee Turnover in Key Functions: Elevated turnover could signal decreased process knowledge or lowered morale.
- Number of Security Incidents: Spikes in phishing attempts or malware intrusions may indicate bigger cyber threats on the horizon.
- Vendor SLA Violations: Repeated supply chain failures highlight potential external dependencies.
By defining thresholds for each KRI, GRC platforms can automatically flag and escalate unusual or risky changes.
7.2 Risk and Control Self-Assessments (RCSAs)
RCSAs involve periodic questionnaires and review sessions where process owners evaluate the design and effectiveness of their controls. They identify new or altered risks, document changes in workflow, and rate control maturity. These self-assessments are crucial for validating day-to-day operations remain consistent with risk appetite and compliance mandates. Self-assessment results often feed into higher-level risk reports, bridging frontline operational insights with executive oversight.
7.3 Control Testing and Continuous Monitoring
Control testing, whether annual, quarterly, or continuous, ensures that key risk-mitigating mechanisms work as expected. In some highly regulated environments, continuous monitoring has emerged as a best practice. For example:
- Continuous Control Monitoring (CCM): Automated checks on privileged user access, financial transaction logs, or system configurations.
- Automated Alerts: Instant emails or dashboard prompts when a control drifts from baseline parameters (e.g., critical system patch not applied).
Because regulators and auditors often request historical evidence of control efficacy, storing these test results within a central GRC repository greatly simplifies compliance reviews.
8. Advanced Methodologies: Scenario Analysis and Stress Testing
In risk-sensitive industries like finance, scenario analysis extends beyond simplified or static risk scoring. Enterprises develop hypothetical but plausible scenarios—such as a major cyberattack striking during peak transaction periods—and estimate potential outcomes across multiple dimensions: financial loss, downtime, reputational impact, and possible regulatory repercussions.
Stress testing simulates extreme conditions (e.g., a severe natural disaster combined with IT infrastructure failure) to reveal systemic vulnerabilities that might remain hidden under normal assumptions. These exercises often align with regulatory expectations (such as those under Basel frameworks) and help allocate capital reserves for operational risk. They also refine business continuity and disaster recovery plans by identifying single points of failure or resource shortfalls.
9. Third-Party and Supply Chain Risk
Operational risk isn’t confined within internal processes. Many critical functions—manufacturing, IT hosting, distribution, raw material sourcing—rely on external partners. Third-party or supply chain risk can manifest in several ways, including data breaches at a vendor, production stoppages due to supplier insolvency, or poor quality control in subcontracted operations. Effective ORM includes:
- Robust Vendor Onboarding: Thorough due diligence and contractual clauses that define expected controls and reporting protocols.
- Continuous Vendor Monitoring: Periodic audits of vendor compliance, performance metrics, and alignment with relevant regulations (e.g., SOC 2 reports for SaaS providers).
- Exit and Contingency Plans: Formal strategies for replacing critical suppliers if they fail to uphold agreed-upon service levels or operational standards.
By integrating third-party risk assessments into the GRC architecture, organizations gain visibility into how external failures might disrupt day-to-day operations and regulatory obligations.
10. Challenges in Building a Mature ORM Function
- Data Silos
In large, global organizations, risk data often resides in disconnected systems—ERP, CRM, HR, or cybersecurity platforms. Consolidating this data into a single GRC environment requires robust integration, a shared taxonomy, and executive sponsorship. - Cultural Hurdles
Operational risk can be perceived as punitive if employees fear retribution for reporting near-misses or inefficiencies. Building a “no-blame culture” that prizes transparency and learning over finger-pointing is essential. - Resource Limitations
Implementing advanced analytics, continuous monitoring, or scenario modeling tools demands skilled personnel and budgetary investments. Some organizations struggle to quantify the ROI of preventing operational crises, making funding approvals difficult. - Regulatory Overlaps
Operating across multiple jurisdictions can lead to duplicative or conflicting requirements. Institutions must harmonize these obligations without doubling administrative burdens or missing local nuances. - Rapid Technological Changes
AI adoption, cloud migration, and IoT expansions introduce new vulnerabilities. Traditional controls may not suffice, and compliance teams must swiftly adapt to protect intellectual property, data flows, and critical infrastructures from novel exploits.

11. Best Practices for Compliance Officers and Risk Leaders
Embrace a Risk-Aware Culture: Encourage open reporting of process gaps and near-misses. Reinforce training programs that keep staff current on regulations and internal policies.
Leverage External Benchmarks and Intelligence: Participate in industry consortia or intelligence-sharing platforms. These insights help validate internal risk ratings, reveal emerging threats, and identify best practices in peer organizations.
Create a Governance Model: Define roles—such as risk committees, escalation paths, and clear lines of accountability—for operational risk. A robust governance model ensures the board and executive management remain informed and proactive.
Conduct Regular Gap Analyses: Align existing controls with prevailing regulations and standards (ISO 31000, COSO, NIST). Document shortfalls, then prioritize remediation steps based on risk-criticality and compliance deadlines.
Enable Advanced Analytics: Invest in data science capabilities or specialized GRC modules. Predictive models can uncover subtle correlations (e.g., spike in service desk tickets forecasting a major system outage) and refine scenario testing accuracy.
12. Advancing Operational Risk Management
Holistic Resilience Frameworks are emerging, integrating ORM with business continuity, enterprise risk management (ERM), and resiliency planning. This approach transcends departmental silos, preparing organizations for large-scale disruptions, including climate-linked catastrophes or geopolitical tensions.
AI-Driven Risk Intelligence and machine learning algorithms can parse vast data sets, flag anomalies in real time, and even recommend corrective measures. However, these technologies must be subject to rigorous validation to avoid biases or false positives.
Regulatory Technology (RegTech) solutions offer automated mapping of regulations to operational processes, minimizing human error and accelerating compliance updates. This is particularly relevant for companies operating in fast-changing regulatory ecosystems, such as fintech or digital health.
Environmental, Social, and Governance (ESG) Risk is also overlapping with operational risk, as stakeholders and regulators increasingly demand accountability for supply chain ethics, carbon footprints, and social responsibility. A future-forward ORM program accounts for these elements to guard against evolving reputational, legal, and operational repercussions.
The Imperative of a Resilient ORM Program
Operational Risk Management is both a regulatory requirement and an organizational imperative that, when robustly implemented, safeguards revenue, reputation, and stakeholder trust. By integrating operational controls into a centralized GRC framework—supported by strong risk taxonomies, comprehensive scenario modeling, continuous monitoring, and a collaborative culture—entities become well-positioned to mitigate disruptions. Compliance officers play a pivotal role, ensuring legal mandates are met, internal policies remain effective, and management decisions are informed by accurate, up-to-date risk data. As industries adopt advanced technologies and regulations grow increasingly stringent, the maturity of an organization’s ORM program could be the determining factor between enduring success and catastrophic failure.
Reduce your
compliance risks

