Integrated Risk management (IRM) Defined
Our conversation has focused on the importance of Integrated Risk Management (IRM) in today's complex business environment. We've explored the core benefits of implementing an effective IRM strategy, such as data reliability, financial efficiency, and strategic clarity.

Why Integrated Risk Management Is Now a Business Imperative
Industry after industry is confronting a fast-evolving risk landscape. Where once risk management meant checking boxes for compliance, today’s challenges include global cyber threats, volatile supply chains, data-privacy regulations, complex financial-reporting mandates, environmental expectations and demands from investors for robust oversight. Against this backdrop, integrated risk management (IRM) has evolved as a comprehensive strategy that unifies risk, compliance, governance and performance into a single, coherent architecture.
Scope and Purpose
IRM’s purpose is to give leadership an enterprise-wide view of exposures while embedding proactive controls into day-to-day decision-making. The scope therefore spans every risk domain, from financial and operational to cybersecurity, ESG and reputation, ensuring that no threat is managed in isolation.
Integrated Risk Management in Financial Compliance: Frameworks and Best Practices
In the financial-services sector, integrated risk management has rapidly emerged as a cornerstone of strategic governance. In today’s fast-evolving regulatory environment, characterised by complex and interconnected risks, organisations can no longer afford to address issues in silos. An integrated approach that manages the full spectrum of risks (credit, market, operational, cybersecurity and compliance) within a unified strategy is essential for long-term resilience and regulatory alignment.
Firms that implement IRM consistently report lower compliance costs, fewer operational disruptions and stronger overall resilience. Recent industry reports show financial institutions using integrated strategies enjoy marked reductions in remediation expenses and improved profitability, largely thanks to proactive mitigation and a stronger risk-aware culture.
Throughout this guide we reference key regulatory frameworks—including the EU’s CRD IV, the global standard ISO 31000 and the Basel III principles—to illustrate how IRM is embedded in modern financial regulation and why it has become a fundamental business imperative. IRM is not a buzzword; it is a proven, strategic approach that helps financial firms navigate the evolving landscape while optimising risk management across their operations.
Understanding Integrated Risk Management
Integrated Risk Management is a strategic, enterprise-level approach to identifying, assessing and addressing risk across all departments and domains. Originally popularised by Gartner, IRM aims to improve decision-making and performance by giving stakeholders a holistic view of the risks the business faces.
- Break down silos – Traditional models treated financial, IT and compliance risks separately. IRM consolidates data and activities so leaders can see interdependencies and act faster.
- Enhance collaboration – By unifying processes, IRM ensures everyone, from front-line employees to the C-suite, shares accountability for risk mitigation and reporting.
- Move beyond GRC – Governance, Risk and Compliance (GRC) frameworks often remain checklist-oriented. IRM, by contrast, embeds risk thinking into everyday operations and strategic planning.
- Adopt six components – Strategy, Risk Assessment, Response, Communication & Reporting, Monitoring and Technology collectively guide a cohesive programme that aligns with corporate goals.
- Embed ISO 31000 principles – The standard stresses that risk management must be integral to all organisational processes, turning a reactive obligation into a proactive, value-driven function.
The key takeaway: integrated risk management is designed to eliminate bureaucracy, not create it. By weaving risk intelligence into strategic planning, project management and corporate culture, organisations anticipate and address threats before they escalate, fostering continuous improvement and resilience.
Linking IRM to Global Regulatory Frameworks
| Framework / Standard | How It Aligns With Integrated Risk Management | Practical Impact |
|---|---|---|
| CRD IV (EU) | Requires capital planning, stress testing and risk-aggregation processes that mirror IRM’s holistic view. | Smoother supervisory reviews, reduced capital add-ons. |
| Basel III | Emphasises integrated measurement of credit, market and operational risks. | More accurate risk-weighted assets, optimised capital allocation. |
| ISO 31000 | Provides overarching principles and a clear process for embedding risk management across the organisation. | Consistent risk language and culture, easier auditability. |
The Evolution of Integrated Risk Management: From Silos to Integration
Historically, separate departments, IT security, finance, legal, and others, owned discrete risk functions, creating siloed and often reactive processes. This fragmented model hindered resource allocation and obscured cross-functional interdependencies. Integrated risk management (IRM) replaces that patchwork with a single, connected framework that:
- Centralises Risk Registers
- Maintains one authoritative source for threats, vulnerabilities, and incident logs.
- Coordinates Governance
- Harmonises leading frameworks—ISO 31000, COSO ERM, HIPAA, PCI DSS, and sector-specific mandates—into one methodology.
- Promotes Continuous Improvement
- Shifts risk management from an annual checklist to an always-on cycle of monitoring, analysis, and adaptive response.
Core Principles and Objectives of an IRM Programme
| Principle | What It Means | Practical Outcome |
|---|---|---|
| Holistic Coverage | Addresses everything from day-to-day operational risks (system outages, vendor failures) to strategic macro risks (geopolitical turmoil, ESG, reputational fallout). | No threat is evaluated in isolation; interdependencies become clear. |
| Alignment with Corporate Strategy | • Board-approved risk appetite sets clear guardrails. • IRM metrics feed directly into strategic planning, R&D budgets, M&A and expansion proposals. |
Decisions balance opportunity and exposure in real time. |
| Regulatory Excellence | • Unified control libraries map each control to multiple regulations. • Automated evidence collection keeps a continuous audit trail. |
Faster audits, lower compliance costs, stronger regulator confidence. |
| Technology Enablement | • Enterprise data orchestration spanning finance, HR, ERP and threat-intel feeds. • AI-driven analytics for predictive modelling, anomaly detection and scenario planning. |
Early insight into emerging threats and data-backed decision-making. |
| Proactive vs Reactive Culture | • KRIs and KPIs warn teams when thresholds near limits. • Management sees certain risks as strategic differentiators, not just liabilities. |
Resilience becomes a competitive advantage, not a cost centre. |
Why Integrated Risk Management Is Essential for Financial Compliance
In highly regulated sectors such as banking, compliance and risk are inseparable. Modern regulators require firms to manage all risks, compliance (AML, data privacy), operational (cybersecurity, fraud, third-party), and strategic (market volatility, climate impact), within a unified integrated risk management framework.
The Regulatory Push for IRM
After the 2008 crisis, global watchdogs concluded that fragmented oversight was a root cause of systemic failure. Regulations like the EU’s Capital Requirements Directive (CRD IV/V) now embed IRM principles:
- Article 76 of CRD IV: “The management body shall be actively involved in and ensure that adequate resources are allocated to the management of all material risks,” explicitly covering financial and non-financial exposures.
- Boards are now personally accountable for enterprise-wide, integrated risk strategies.
For financial institutions, adopting IRM is no longer optional. It is a regulatory mandate that delivers:
- Lower remediation costs via early detection.
- Stronger capital efficiency thanks to holistic stress testing.
- Enhanced stakeholder trust through transparent, board-level oversight.

IRM vs. GRC vs. ERM: Understanding the Differences
- GRC (Governance, Risk, Compliance): Historically compliance-led, with robust policy libraries, control mapping, and auditing processes. GRC ensures that governance structures meet regulatory obligations but may not provide the same strategic orientation as IRM.
- ERM (Enterprise Risk Management): A broad-based risk methodology that addresses enterprise-wide threats and opportunities. ERM frameworks (e.g., COSO ERM) look at risk in relation to organizational strategy.
- IRM (Integrated Risk Management): Encompasses GRC and ERM attributes while adding deeper data integration, real-time analytics, cohesive technology platforms, and forward-looking scenario modeling. IRM also emphasizes synergy between operational and strategic risks, bridging the gap between day-to-day risk controls and long-term objectives.
Integrating Risk Governance into Corporate Structure
In addition to risk oversight, CRD IV requires large banks to establish independent risk committees and appoint a Chief Risk Officer (CRO) to integrate risk management directly into the governance structure. This is a key shift: compliance with prudential rules such as capital and liquidity requirements can no longer be handled as isolated tasks. These requirements must be part of a unified risk governance framework.
The Basel Committee on Banking Supervision echoes this need for integrated risk governance in its Corporate Governance Principles for Banks (2015), which state that “the board has ultimate responsibility for the bank’s risk management and compliance obligations.” Managing risk and ensuring regulatory compliance are now seen as joint responsibilities at the highest levels of corporate governance, reinforcing the necessity of IRM.
Industry-Wide Integration of Risk Management
Beyond banking, the adoption of IRM extends to the insurance sector through Solvency II in Europe. The Own Risk and Solvency Assessment (ORSA) process compels insurers to assess their entire risk profile and solvency needs in a forward-looking manner, integrating data from underwriting, investments, operations, and strategy. According to industry experts, ORSA requires a “joined-up approach” across the company, helping boards make sound strategic decisions and embedding risk awareness throughout the organization.
Proactive vs. Reactive Compliance
An integrated ERM system, such as ISO 31000, plays a critical role in reducing the risk of non-compliance. Unlike traditional risk management, where compliance is often a reactive response to regulation, IRM allows financial institutions to anticipate and address regulatory issues as part of their overall risk strategy. By embedding compliance into day-to-day decision-making, IRM ensures that regulatory controls, such as anti-money laundering policies, data protection measures, and conduct risk policies, are incorporated from the outset.
This proactive approach leads to fewer surprises, such as sudden audit findings or regulatory penalties, and aligns compliance efforts with business goals. This alignment creates a more agile and competitive financial institution, where compliance is not a separate mandate but integrated with broader business strategies.
Supporting Resilience in a Rapidly Changing Regulatory Environment
The regulatory landscape is not static; it evolves with emerging risks such as operational resilience, cybersecurity, and Environmental, Social, and Governance (ESG) concerns. IRM provides the flexibility to incorporate new risk domains quickly into the existing risk management framework. For instance, the EU's Digital Operational Resilience Act (DORA) requires financial institutions to implement comprehensive ICT risk management frameworks. Under an IRM framework, financial institutions can integrate these new requirements into their established governance structures, rather than creating separate programs for each new risk category.
Similarly, IRM enables financial institutions to swiftly incorporate climate-related financial risks, as regulatory bodies like the European Central Bank are increasingly emphasizing the importance of addressing climate risks within overall risk management strategies.
Regulatory Frameworks and Standards Shaping Integrated Risk Management (IRM)
One of the key strengths of Integrated Risk Management (IRM) is its ability to serve as a unifying umbrella for a variety of frameworks and standards that organizations may already be following. Rather than conflicting with established risk or compliance methodologies, IRM brings them together into a cohesive structure, ensuring alignment across the organization. Below is an overview of several important frameworks, regulations, and standards—some well-known, others less commonly cited—that contribute to the regulatory depth of IRM in financial services.
1. Basel III and the EU Capital Requirements (CRR/CRD)
The Basel III framework and the EU’s Capital Requirements Regulation (CRR) and Capital Requirements Directive (CRD) set prudential rules for banks globally. These regulations mandate that financial institutions implement robust internal risk management practices, covering all material risks and subject to supervisory review under Pillar 2 of Basel III. CRD V further mandates board-level oversight and the integration of risk data through mechanisms like the Internal Capital Adequacy Assessment Process (ICAAP).
In addition to these global regulations, national implementations such as Germany’s MaRisk provide detailed guidance on managing a comprehensive range of risks, including credit, market, liquidity, operational, and outsourcing risks. This principles-based framework helps smaller firms apply IRM in a proportionate way, demonstrating how these regulations translate IRM principles into practical actions.
2. Solvency II and the Insurance Core Principles (Global)
For the insurance sector, Solvency II in Europe enforces IRM by requiring insurers to assess their entire risk profile through processes like Own Risk and Solvency Assessment (ORSA). This framework ensures that risk and capital management are integrated into decision-making.
Globally, the International Association of Insurance Supervisors (IAIS) has established core principles for Enterprise Risk Management (ERM) frameworks at insurers. These principles require insurers to identify, monitor, and control risks across their enterprise. Similarly, in the U.S., the National Association of Insurance Commissioners (NAIC) mandates ORSA requirements, promoting a consistent ERM approach across all insurers.
3. COSO ERM – Integrated Framework
The COSO Enterprise Risk Management (ERM) Framework is one of the most widely recognized best-practice guidelines for IRM. Updated in 2017, COSO ERM explicitly focuses on integrating risk with strategy and performance, transforming ERM from a compliance-focused exercise into a strategic tool. COSO highlights the importance of governance, culture, strategy, performance, review, and communication — embedding risk considerations into business strategy.
COSO’s guidance emphasizes effective risk governance through robust communication of risk information, ensuring that risk insights reach the board level. In 2020, COSO released supplemental guidance on managing compliance risks within an integrated ERM approach, underscoring that compliance risk should not be managed in isolation but alongside other organizational risks.
4. ISO 31000 – Risk Management Guidelines
ISO 31000:2018 is a globally recognized standard that complements IRM by providing principles, a framework, and processes for managing risks applicable to any industry. Key principles of ISO 31000 include structured and comprehensive risk management, customized to the organization’s context, inclusive engagement with stakeholders, responsiveness to change, and continuous improvement.
For financial institutions, aligning risk management practices with ISO 31000 demonstrates adherence to international best practices and helps ensure compliance with regulatory expectations. Notably, ISO 31000’s approach to risk management directly supports regulatory compliance, minimizing the chances of compliance failures by addressing risks in a holistic manner.
5. BCBS 239 – Effective Risk Data Aggregation and Reporting
The Basel Committee’s BCBS 239 standard, issued in 2013, focuses on enhancing risk data aggregation and internal risk reporting practices in large banks, particularly for Global Systemically Important Banks (G-SIBs). This standard emphasizes the need for banks to invest in integrated data systems capable of rapidly aggregating and reporting risk data across business lines. By improving data architecture, BCBS 239 enables more informed decision-making and supports true IRM.
6. OECD Corporate Governance Principles
The OECD Corporate Governance Principles, updated in 2023, place greater emphasis on risk management and internal controls as integral elements of good governance. These principles, while high-level, are embedded in national governance codes, driving regulatory expectations across countries. They reinforce the idea of board-level responsibility for risk, the necessity of risk committees, and the transparent disclosure of risk exposures, all of which support the implementation of IRM.
7. DORA and NIS2: Cyber and ICT Risk Management
The EU’s Digital Operational Resilience Act (DORA) and NIS2 Directive emphasize the importance of integrated risk management for ICT and cyber risks in critical sectors. DORA specifically mandates financial entities to implement comprehensive ICT risk management frameworks. Under IRM, these digital risks are seamlessly integrated into existing risk governance structures, rather than requiring separate risk programs. This integration helps financial institutions stay compliant while managing digital risks as part of their broader operational resilience.
8. ISO 37301 – Compliance Management Systems
The ISO 37301:2021 standard, which succeeds ISO 19600, provides a risk-based approach to compliance management systems. It encourages financial firms to assess compliance risks and opportunities in a structured manner, integrating compliance controls into daily operations. A firm that aligns with ISO 37301 naturally incorporates compliance risks into its IRM framework, ensuring continuous improvement of compliance controls.
9. National Guidelines and Codes
Many countries have national guidance that incorporates IRM principles, even if the guidance is not explicitly labeled as such. For example, the UK’s Senior Managers & Certification Regime (SMCR) holds executives accountable for failures in their respective areas, incentivizing an integrated oversight culture. Similarly, Singapore’s Monetary Authority (MAS) guidelines often stress the importance of enterprise risk management in financial institutions, providing clear expectations for risk governance.
To visualize the landscape, consider the following table of select frameworks and their focus:
| Framework / Regulation | Scope & Sector | IRM Focus / Requirements |
|---|---|---|
| Basel III & CRD IV/V (EU) | Banking (Global/EU) | Holistic risk governance (Board oversight of all material risks risk committees, capital & liquidity integrated with risk appetite). Banks must implement ICAAP/ILAAP linking risk to capital planning. |
| Solvency II (ORSA) | Insurance (EU) | Enterprise risk-and-solvency assessment requiring joined-up risk evaluation and forward-looking capital adequacy, embedded in decision making |
| COSO ERM Framework (2017) | All sectors (Global) | Widely-used voluntary framework integrating risk with strategy and performance. Emphasises risk culture, objective-setting, and linking risk management to value creation. Provides common language and components for IRM. |
| ISO 31000:2018 | All sectors (Global) | International standard outlining principles (Integrated, Structured, Customized) and a generic process for risk management. Helps embed risk management into processes and facilitates compliance with regulatory risk requirements |
| BCBS 239 Principles | Banking (Global G-SIBs/D-SIBs) | Standard on risk-data aggregation & reporting. Requires banks to unify data across silos to produce accurate, timely risk reports, enhancing decision-making and enabling enterprise-wide risk insight |
| DORA (EU) | Financial-sector ICT/cyber (EU) | Regulation enforcing integrated management of ICT risks. Firms must have comprehensive ICT risk management within the overall risk framework, report incidents, test resilience, and oversee third-party tech providers |
| ISO 37301 (Compliance Mgmt) | All sectors (Global) | International standard for compliance programmes using a risk-based approach. Complements IRM by ensuring compliance risks are systematically identified, controlled and integrated into enterprise risk assessments. |
| OECD & National Governance Codes | Corporate Governance (Global/Local) | Emphasise board responsibility for risk and internal control. For example, Basel/OECD principles require boards to ensure robust risk management and compliance as part of governance |
(Table: Key frameworks and regulations underpinning integrated RISK MANAGEMENT. These illustrate how IRM is embedded in financial rules and standards across domains.)
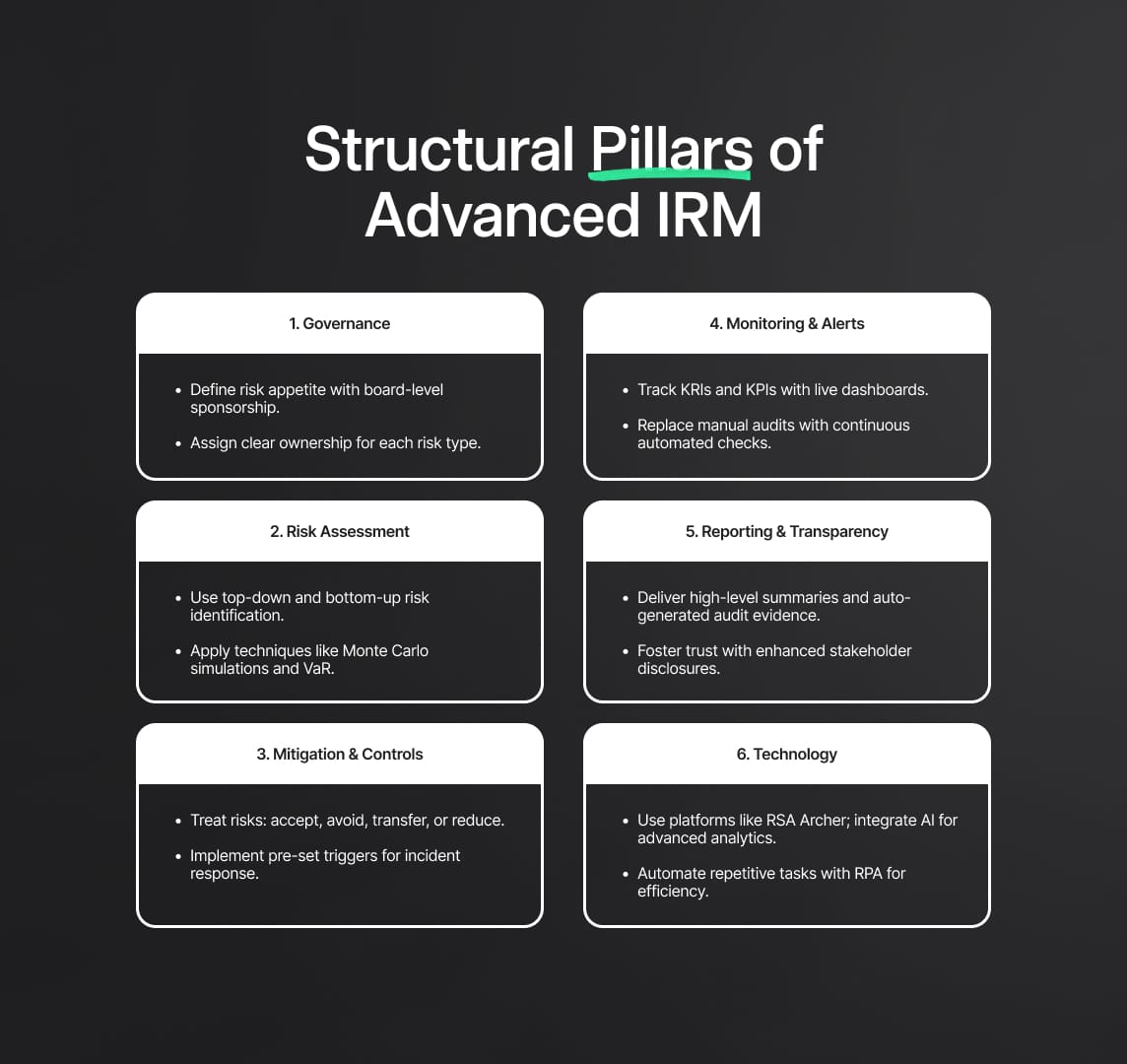
Enterprise-Wide Integrated Risk Management Playbook
1. Achieving Depth in Risk Quantification & Scenario Planning
1.1 Scenario Analysis
Organisations craft plausible futures—natural disasters, currency crises, cyber-ransomware attacks—and assess how each scenario would affect operations, liquidity, brand value and stakeholder relationships. These exercises help prioritise remediation, resource allocation and crisis drills.
1.2 Stress Testing in Integrated Risk Management
- Reverse Stress Tests – define the worst-case outcome first, then work backwards to the conditions that could cause it.
- Liquidity & Capital Stress – focus on capital buffers under adverse market swings, interest-rate volatility or large-scale credit defaults.
- Operational Resilience Stress – simulate extended data-centre outages or labour shortages to validate business-continuity protocols.
1.3 Risk Modelling & Analytics
- Prescriptive Analytics – recommends mitigation actions (e.g., shifting production when a supply-chain node’s risk rises).
- Behavioural Analysis – monitors for unusual employee or vendor behaviour, such as repeated access to sensitive files or contract anomalies.
2. Operationalising Integrated Risk Management Across Multiple Lines of Defence
| Line of Defence | Role & Responsibilities | Tools & Techniques |
|---|---|---|
| First Line – Operational Management | Department managers and process owners identify and manage risks in daily operations. | Continuous Controls Monitoring (CCM) for real-time anomaly detection. |
| Second Line – Risk, Compliance & Control | Formal risk and compliance teams set frameworks, define thresholds and provide oversight. | Specialised analyses (e.g., vendor-risk evaluations). |
| Third Line – Internal Audit | Independently evaluates IRM design and operational effectiveness. | Control testing, maturity reviews. |
| Fourth Line – External | External auditors and regulators verify risk data and controls. | Regulatory exams, assurance reports. |
3. Building a Culture That Embraces Integrated Risk Management
| Pillar | Key Actions |
|---|---|
| Education & Training | Tailored modules for all staff—from new hires to board members—on recognising, escalating and documenting risk. |
| Communication & Transparency | Accessible risk dashboards; frequent updates on risk status and near-misses. |
| Incentives & Recognition | Rewards for proactive risk identification; risk metrics included in performance reviews. |
4. Technological Foundations: IT Architecture for Integrated Risk Management
- Data Management Layer
- Data Lake/Warehouse aggregates structured & unstructured data (transaction logs, emails, social feeds).
- Metadata & Cataloguing ensures provenance for audits and investigations.
- Integration & API Strategy
- RESTful APIs link IRM platforms with ERP, CRM, HR and custom apps.
- Event Streaming ingests high-frequency IoT or security-log data in real time.
- Security & Access Controls
- Zero-Trust Architecture verifies every request by identity, device and context.
- Encryption & Tokenisation protects sensitive risk data with role-based decryption.
- Automation & Orchestration
- RPA automates repetitive tasks (evidence collection, control checks).
- Orchestration Platforms coordinate workflows, escalations and automatic risk-register updates.
5. Implementation & Scaling Roadmap for Enterprise-Wide Integrated Risk Management
5.1 Current-State Analysis
- Conduct gap assessments across risk functions, processes and technology.
- Engage stakeholders (finance, cyber-security, legal) to surface pain points.
5.2 Establish Strong Governance & Culture
- Form Enterprise Risk Committees with cross-functional membership.
- Create board-level risk committees; appoint a Chief Risk Officer (CRO) with enterprise authority.
- Embed the updated Three Lines Model roles and celebrate sound risk decisions.
5.3 Develop a Unified Risk Framework & Taxonomy
- Define risk categories (financial, strategic, operational, compliance) with metrics (likelihood, impact, RAG).
- Publish an enterprise risk policy aligned with COSO ERM or ISO 31000 that details identification, scoring, response and monitoring.
- Ensure specialised outputs (e.g., NIST cyber-metrics) map back to the central risk register.
5.4 IRM Strategy Definition
- Outline short-term wins (e.g., automating a key audit process) and long-term transformations (full platform integration).
- Identify success metrics such as fewer repeat incidents, faster audits and higher compliance ratings.
5.5 Platform Selection & Technology Enablement
- Choose an IRM suite or modular stack that fits organisational complexity, integration needs and regulatory library updates.
- Implement GRC/IRM software to automate workflows, surface real-time dashboards and aggregate data.
5.6 Structured Phasing
- Start with high-priority domains (cyber-security, regulatory compliance) then scale once foundations stabilise.
5.7 Integrate Compliance into ERM Activities
- Add compliance risks (AML, sanctions, privacy) to enterprise assessments.
- Form joint risk–compliance–legal committees; align monitoring plans with assessment results.
5.8 Set Risk Appetite & Link to Strategy
- Board-approved statements combining quantitative limits and qualitative goals.
- Use appetite thresholds to guide product launches, market entries and strategic moves—aligning with EBA/ECB expectations.
5.9 Communication, Training & Change Management
- Host workshops on new IRM tools, risk matrices and dashboards; provide ongoing coaching.
5.10 Continuous Monitoring, Improvement & Evidence
- Integrate KRIs into performance dashboards; conduct annual strategic-risk reviews, audits and benchmarking.
- Maintain policies, committee minutes, board reports, incident logs and remediation trackers to satisfy regulators.
6. Measuring the ROI of Integrated Risk Management
| Benefit Area | Outcomes |
|---|---|
| Reduced Compliance Costs | Automated evidence gathering; consolidated audits lower consulting fees. |
| Fewer Incidents & Lower Impact | Early vulnerability detection prevents crises, reputational damage and supply-chain setbacks. |
| Strategic Decision-Making | Greater risk transparency enables agile scenario planning and balanced risk-return choices. |
| Stakeholder Trust & Brand Value | Robust IRM builds credibility with investors, regulators and customers, improving credit ratings and insurance terms. |
7. Common Pitfalls & How to Avoid Them
| Pitfall | Risk | IRM-Aligned Mitigation |
|---|---|---|
| Over-complication | Analysis fatigue from too many frameworks at once. | Roll out in measured phases prioritising critical risks. |
| Poor Data Quality | Misguided scoring and analytics. | Invest in rigorous data governance, validation and cleansing. |
| Cultural Resistance | Perceiving risk as mere box-checking. | Consistent communications, training and visible leadership advocacy. |
| Lack of Board Engagement | Budget shortfalls and misalignment. | Provide real-time dashboards and financial-impact analyses to keep executives invested. |
| Underestimating Emerging Threats | Blind-sided by zero-day exploits or AI-driven attacks. | Continuous threat-intelligence monitoring and flexible IRM frameworks. |

15. Why Integrated Risk Management is a Must-Have?
Integrated Risk Management is no longer a choice but an essential operational paradigm for complex organizations. By unifying data sources, standardizing control frameworks, adopting cutting-edge analytics, and fostering a risk-aware culture, IRM dismantles silos and unlocks proactive, value-centric decisions. This approach:
- Safeguards Reputation: Minimizes unexpected crises and assures stakeholders of robust governance.
- Streamlines Compliance: Collates obligations into one cohesive system, simplifying audits and reducing administrative burdens.
- Drives Innovation: Empowers leaders to confidently capitalize on new markets, digital initiatives, or partnerships without blindsiding risk exposure.
Modern enterprises that successfully implement Integrated Risk Management exhibit resilience against operational disruptions, regulatory censure, and market volatility, emerging more agile and competitive as a result. By embracing these practices—supported by robust technology platforms, well-trained personnel, and strong executive endorsement—an organization can transform risk from a burden into a strategic advantage.
Reduce your
compliance risks

