Operational Resilience Playbook: DORA, NIS2 & GDPR Compliance
Operational resilience for financial and tech sectors encompasses DORA, NIS2, GDPR and Basel III mandates, integrating ICT risk governance, incident notification, threat-led testing, third-party controls and GRC automation to uphold critical service continuity and regulatory compliance.

Operational Resilience: A Board-Level Imperative for Digital-First Finance
In the always-on world of digital finance, operational resilience is no longer a nice-to-have, it is mission-critical. Banks, fintechs, insurers, and market infrastructures face escalating cyber-attacks, technology glitches, and systemic shocks (such as global pandemics) that can halt essential services. To keep the financial system stable, regulators have introduced robust rules, most notably the EU’s Digital Operational Resilience Act (DORA), the revised NIS2 Directive, GDPR, and global prudential frameworks like Basel III, that demand firms prove they can withstand, adapt to, and rapidly recover from severe disruption.
This guide shows you how to build digital operational resilience under those regimes. You will find:
- the regulatory back-story behind DORA, NIS2, GDPR, and Basel III
- practical implementation steps and risk-management best practices
- the strategic role of GRC software in automating compliance and reporting
What “Operational Resilience” Means in Practice
Operational resilience is an organisation’s capacity to prevent, respond to, recover from, and learn after disruption so critical services stay online. For finance, that means payments clear, trades settle, and customer data remains protected—even when cybercriminals strike or a key cloud provider goes dark. Supervisors emphasise that resilience is the outcome of mature risk management, robust business-continuity planning, and continuous improvement.
High-profile failures highlight the stakes. A defective CrowdStrike update on 19 July 2024 knocked out Windows systems worldwide, grounding airlines and freezing banking platform, a vivid example of third-party ICT risk with cross-sector consequences. These incidents, together with the COVID-19 crisis and successive ransomware waves, spurred policymakers to tighten digital-continuity rules, culminating in DORA and NIS2.
Why Governance, Risk & Compliance (GRC) Matters
Achieving operational resilience extends beyond the IT function. It requires coordinated governance, integrated risk-assessment, disciplined cybersecurity, rigorous third-party oversight, and well-rehearsed incident-response. The sections that follow map the major regulations shaping digital resilience and explain how they intersect, so you can create a single, streamlined compliance programme rather than a patchwork of point-solutions.
EU Digital Operational Resilience Act (DORA): Regulation (EU) 2022/2554
Status & timeline: DORA entered into force on 16 January 2023 and will be directly applicable from 17 January 2025. From that date every in-scope firm must be able to demonstrate digital operational resilience end-to-end.

Why DORA changes everything
- Single rule-book for financial-sector cybersecurity. DORA harmonises requirements that were previously scattered across 15+ EU texts, closing gaps that let ICT incidents at one firm or vendor cascade across the market.
- Lex specialis over NIS2. Where provisions overlap, the sector-specific DORA prevails over the horizontal NIS2 Directive, eliminating double reporting.
- Third-party oversight. Critical ICT service providers (CTPPs), for example, hyperscale cloud or core-banking vendors, will, for the first time, be supervised directly by the European Supervisory Authorities (EBA, ESMA, EIOPA).
Who must comply
DORA captures 21 categories of EU financial entities, including banks, insurers, reinsurers, asset-managers, payment & e-money institutions, investment firms, crypto-asset service providers, trading venues, central counterparties and more.
It also applies to any ICT-service provider deemed “critical” to those entities’ operations, cloud hosts, core-banking platforms, data-analytics or network providers, bringing the entire digital supply-chain inside the regulatory perimeter.
The Five Pillars of DORA Compliance
| Pillar | What the regulation requires | Practical takeaway |
|---|---|---|
| ICT Risk Management | Maintain a full-lifecycle framework: continuous risk identification, secure-by-design change control, and annual BCP/DR testing. | Shift from reactive patching to proactive resilience engineering. |
| Incident Management & Reporting | Detect, classify and report major ICT incidents to the competent authority within strict timelines; notify affected clients. | Build an incident taxonomy and automate regulatory reporting workflows. |
| Digital Operational Resilience Testing | Conduct regular penetration tests, vulnerability scans, and threat-led penetration tests every three years for large firms; remediate all gaps. | Treat threat-led testing results as board-level KPIs. |
| ICT Third-Party Risk Management | Inventory all suppliers, perform pre-contract due diligence, embed exit and resilience clauses, monitor performance, and report critical providers. | Tie SLA metrics to recovery-time and resilience objectives. |
| Information Sharing | Join trusted communities to exchange cyber-threat intelligence and best practices under secure, compliant arrangements. | Participate in sector ISACs for early warning of emerging threats. |
Supervision, enforcement & penalties
National financial supervisors—co-ordinated by the three ESAs, can carry out on-site inspections, issue remedial orders, suspend activities, and impose substantial fines:
- Firms: up to 2 % of total annual worldwide turnover or 1 % of average daily turnover.
- Individual managers: up to €1 million.
- Critical ICT providers: up to €5 million or 1 % of average daily turnover.
Next steps for operational resilience leaders
- Gap-analyse today, remediate by Q1 2025. Align existing ISO 27001, NIST or Basel frameworks with DORA’s five pillars.
- Map your entire digital supply chain. Early engagement with potential CTPPs reduces supervisory surprises.
- Automate evidence. Use GRC platforms to capture controls, test results and incident logs in one audit-ready dashboard.
- Embed “resilience by design.” Push DORA requirements into DevOps pipelines so new releases launch compliant.
- Board reporting. Translate ICT metrics into risk-appetite language the board can own.
With the 17 January 2025 deadline fast approaching, firms that operationalise these steps now will turn compliance into competitive advantage, and demonstrate the experience, expertise, authoritativeness and trustworthiness regulators, partners and search-engines alike expect in the digital-finance era.
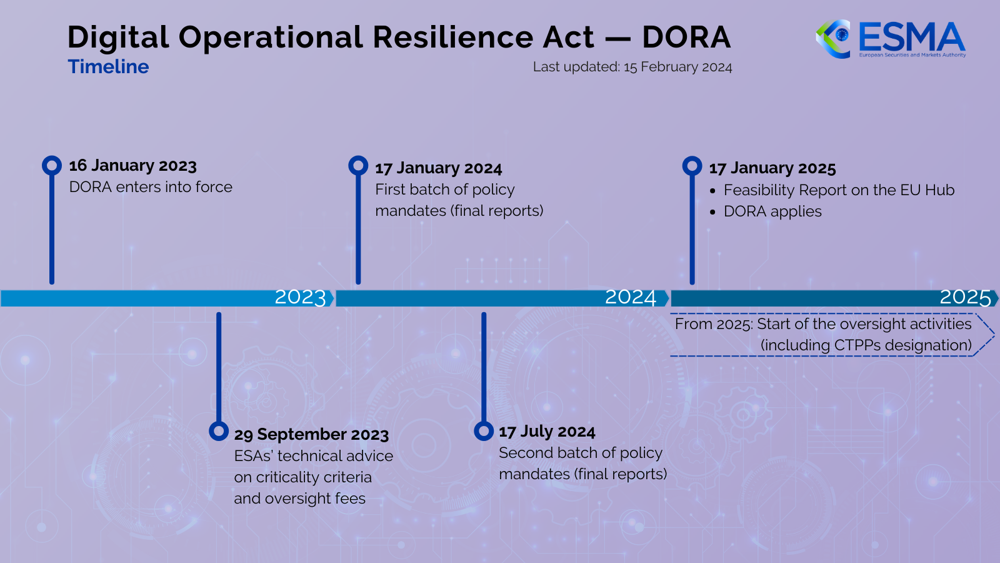
DORA Implementation Timeline – Key dates for the Digital Operational Resilience Act (Regulation (EU) 2022/2554). DORA entered into force in January 2023, and by January 17, 2025, its requirements become mandatory across the EU financial sector.
NIS2 Directive (Directive (EU) 2022/2555): A Union-Wide Baseline for Operational Resilience
Status & timeline: NIS2 was adopted in late 2022, entered into force on 16 January 2023, and had to be transposed by the Member States no later than 17 October 2024. As of early 2025 the Commission has launched infringement procedures against 23 countries that missed the deadline, signalling that enforcement is imminent.
Who falls under NIS2
| Entity class | Typical size threshold | Examples of in-scope sectors (18 in total) |
|---|---|---|
| Essential entities | > 250 employees or > €50 m turnover / €43 m balance sheet | energy, transport, large banks, major hospitals, digital infrastructure |
| Important entities | ≥ 50 employees or ≥ €10 m turnover | postal & courier, cloud and data-centre services, social-media, critical manufacturing, mid-tier public administration |
Micro- and small enterprises are generally exempt unless they perform high-risk functions (e.g., DNS or trust-service operators).
Regulatory Objectives
- Establish a high common level of cybersecurity across the EU and reduce the patchwork left by the 2016 NIS1.
- Impose uniform risk-management, incident-reporting, and governance duties.
- Strengthen cross-border operational resilience through coordinated supervision, the CSIRTs Network and the EU-CyCLONe crisis hub.
Core Obligations for Covered Entities
| Domain (Annex I) | What you must do (non-exhaustive) |
|---|---|
| Cyber-risk management | Run continuous risk assessments; encrypt critical data; enforce MFA; patch systems; embed secure-SDLC. |
| Business continuity & crisis preparedness | Maintain up-to-date BCP/DR plans, offline backups, and rapid service-restoration playbooks. |
| Incident reporting | Notify the national authority within 24 h (initial), 72 h (detailed), and 1 month (final/root-cause). |
| Supply-chain security | Vet suppliers, write resilience clauses into contracts, and monitor third-party cyber posture. |
| Governance & training | Board approves policy; executives are personally accountable for compliance and can be sanctioned for negligence. |
Supervision & Penalties
- Essential entities: fines up to €10 m or 2 % of global turnover, whichever is higher.
- Important entities: up to €7 m or 1.4 % of global turnover.
- Competent authorities may also order specific remedial actions or temporarily disqualify executives in cases of gross negligence.

How NIS2 Interacts with DORA
For EU financial institutions, DORA is lex specialis: its sector-specific ICT-risk rules override overlapping NIS2 provisions. Complying with DORA therefore satisfies equivalent NIS2 duties, but firms must still address any NIS2 requirements that DORA does not explicitly cover. Conversely, many suppliers that finance relies on, telecoms, cloud, logistics, are governed by NIS2, so aligning procurement and third-party monitoring with both frameworks is vital for end-to-end operational resilience.
Action checklist for 2025
- Map applicability: classify each business unit as essential, important or out of scope.
- Close reporting gaps: automate the 24 / 72 / 30-day notification workflow.
- Update supply-chain contracts: embed NIS2-level security clauses and right-to-audit provisions.
- Elevate board ownership: brief executives on personal liability and integrate cyber-KPIs into risk appetite.
- Test and refine: exercise BCP and crisis-management procedures alongside national CSIRT drills.

GDPR (Regulation (EU) 2016/679): Data-Protection Obligations That Underpin Digital Operational Resilience
In force since 25 May 2018, GDPR is a horizontal regulation that intersects directly with DORA and NIS2. Although drafted for privacy, it hard-wires security and service continuity into EU law—requirements every financial-sector firm must weave into its operational-resilience programme.
Security & Resilience Duties (Articles 5 & 32)
- Implement “appropriate technical and organisational measures” to guarantee the confidentiality, integrity and availability of personal data, including the “ongoing … resilience of processing systems and services.”
- Typical controls: encryption at rest/in transit, MFA, least-privilege access, secure-by-design development, geo-redundant backups, and tested disaster-recovery plans.
- These controls map neatly to DORA’s ICT-risk pillar and NIS2’s Annex I domains, allowing one consolidated control set to satisfy all three regimes.
72-Hour Personal-Data-Breach Notification (Article 33)
- Notify the supervisory authority within 72 hours of becoming aware of a personal-data breach, unless you can demonstrate “unlikely risk” to data subjects.
- Where a breach is likely to harm individuals, you must also inform them “without undue delay.”
- In practice, a single incident (e.g., ransomware) may trigger three parallel reports:
- DORA → national financial supervisor (operational disruption)
- NIS2 → cyber authority/CSIRT (critical-service outage)
- GDPR → Data Protection Authority (personal-data loss)
Streamline your incident-response playbooks so evidence is captured once and reused across regulators.
Administrative Fines & Management Liability
| Regime | Maximum corporate fine | Potential individual exposure |
|---|---|---|
| GDPR | €20 m or 4 % of worldwide turnover (whichever is higher) | DPOs and senior managers can be investigated or sued for negligence |
| DORA | 2 % of turnover (firms) / €1 m (managers) | — |
| NIS2 | 2 % (essential) / 1.4 % (important) | Temporary management bans |
GDPR’s ceiling is the highest of the trio, underscoring why privacy controls are core to overall resilience.
Impact on Financial-Sector Operational Resilience
- Data availability = service availability. Article 32’s resilience clause means backup, restore and fail-over capabilities must meet the same RTO/RPO targets used for DORA.
- Integrated risk assessments. When you score ICT threats for DORA, include privacy impact so one risk register feeds both regimes.
- Unified control library. Map ISO 27001/NIST controls to GDPR, DORA and NIS2 to avoid duplication.
- Board reporting. Present privacy and operational-resilience metrics side-by-side; senior management is accountable under all three laws.
2025 Action Plan
- Refresh your Article 32 gap analysis against DORA’s five pillars and NIS2 Annex I.
- Harden incident-response SLAs to guarantee 72-hour breach reporting and simultaneous DORA/NIS2 notifications.
- Run combined tabletop exercises (ransomware + data exfiltration) to test cross-regime compliance.
- Automate evidence collection, log retention, access reviews, encryption status, in a GRC platform for audit-ready proof.
Basel III: Prudential Capital as a Backbone of Operational Resilience
Basel III, the global prudential standard finalised in 2017 and phased-in from 2023, is best known for tougher capital, liquidity and stress-testing rules. Yet its treatment of operational risk, and the Basel Committee’s 2021 Principles for Operational Resilience—make it a critical pillar of today’s digital-resilience agenda.
How Basel III embeds Operational-Risk capital
| Element | What it means for resilience |
|---|---|
| Standardised Approach for Operational Risk | From 1 Jan 2023, every internationally-active bank must hold capital calculated via a single, loss- and business-indicator-based formula. The buffer covers losses from cyber-attacks, technology failures, or process breakdowns. |
| Link to Pillar 2 (SREP) | Supervisors may impose extra capital or remediation plans when ICT controls, BCP, or governance are weak. |
| Stress-testing & scenario analysis | Banks must test extreme but plausible events, e.g. a major cloud-provider outage, and quantify capital impact. In 2024, the ECB ran a cyber-resilience stress test on 109 euro-area banks. |
Basel Committee Principles for Operational Resilience
The Basel Committee distilled seven principles to ensure banks can “withstand, adapt to and recover from severe adverse events” such as pandemics, cyber incidents or technology outages: governance; operational-risk management; business-continuity planning & testing; mapping of critical operations and interdependencies; third-party dependency management; incident management; and resilient cyber/ICT controls.
Why this matters for Digital-Finance firms
- Capital incentivises prevention. Fewer outages and data-loss events lower loss-history inputs, reducing future operational-risk capital under the standardised formula.
- Supervisory scrutiny is converging. Weak resilience now attracts both capital add-ons (Basel III Pillar 2) and conduct penalties under DORA and NIS2.
- Global consistency. Basel standards shape national rules, from the ECB’s ICT-risk methodology to the UK PRA’s “impact-tolerance” regime, aligning them with EU digital-resilience laws.
Bridging Basel III, DORA & NIS2
| Topic | Basel III expectation | How DORA/NIS2 build on it |
|---|---|---|
| Capital buffer | Quantify losses & hold solvency shock-absorber | DORA/NIS2 set process controls; Basel ensures financial capacity |
| Mapping & testing | Identify critical operations; run scenario tests | DORA enforces TLPT; NIS2 mandates BC/DR exercises |
| Third-party risk | Map dependencies & ensure substitutes | DORA adds direct ESA oversight of critical ICT providers |
Comparing Key Digital Resilience Regulations and Frameworks
The following table provides a high-level comparison of the scope, focus, and enforcement of major digital resilience regulations/frameworks discussed:
Quick-View: Core EU & Global Frameworks for Digital Operational Resilience
| Framework | Who’s in scope? | What it demands | Key date | Enforcement / penalties* |
|---|---|---|---|---|
| DORA (Reg. EU 2022/2554) | 21 types of EU financial entities + their critical ICT providers | ICT-risk lifecycle, 72 h major-incident reporting, threat-led testing, strict third-party oversight, threat-intel sharing | Fully applicable 17 Jan 2025 | Fines up to 2 % global turnover (firms) or €5 m (CTPPs); on-site inspections, activity suspensions |
| NIS2 (Dir. EU 2022/2555) | Essential & important entities in 18 critical sectors (energy, transport, banking, health, digital infra, etc.) | Cyber-risk & BC/DR controls, 24 / 72 / 30-day incident notifications, supply-chain security, board accountability | National laws due 17 Oct 2024; applies from Oct 2024 | Essential: up to €10 m / 2 %; Important: €7 m / 1.4 % + executive liability |
| GDPR (Reg. EU 2016/679) | Any org processing EU personal data (sector-agnostic, extra-territorial) | “State-of-the-art” technical & organisational measures, privacy-by-design, 72 h data-breach notice | In force 25 May 2018 | Tier-1 fines up to €20 m / 4 %; compensatory claims by data subjects |
| Basel III + 2021 Resilience Principles | Banks worldwide (via national prudential rules) | Capital for operational risk, mapping of critical ops & third parties, scenario-based stress tests, robust BC/DR & governance | Final Basel III reforms 2023-25 | No fixed fines; supervisors can impose capital add-ons, restrict dividends, mandate remediation |
* Percentages refer to total annual worldwide turnover.
How they fit together: DORA (finance-specific) and NIS2 (cross-sector) hard-wire cybersecurity and continuity duties; GDPR layers privacy-focused security; Basel III ensures banks hold capital and run stress tests to absorb the financial impact of operational shocks. Combined, they create a 360° resilience stack that regulators—and search engines—expect organisations to master.

Implementing Operational Resilience: Step-by-Step Compliance Roadmap
Achieving compliance with DORA, NIS2, GDPR, Basel principles, and allied standards is a multi-disciplinary mission. It demands tight coordination across IT, risk, compliance, and business leadership. Follow the workflow below to embed operational resilience at the heart of your organisation and satisfy every regulatory mandate.
Run a Regulatory Gap Assessment
- Map every applicable requirement from DORA, NIS2, GDPR, Basel III, national guidance, and sector rules.
- Compare those obligations against existing policies, controls, and metrics.
- Pinpoint shortfalls: e.g., missing ICT-risk governance, inadequate breach-reporting SLAs, or limited third-party oversight—to generate a clear remediation backlog.
Strengthen Governance & Accountability
- Create or empower a cross-functional Operational Resilience Committee that includes the CISO, CIO, COO, CRO, Data Protection Officer, and business heads.
- Obtain formal board approval for an enterprise-wide resilience strategy; embed related KPIs in executive scorecards.
- Designate single-point-of-accountability roles for ICT risk, data protection, and business continuity.
Establish a DORA-Ready ICT-Risk Framework
- Build a lifecycle approach covering identification, protection, detection, response, and recovery.
- Define risk-appetite thresholds and align control libraries with DORA and NIS2 clauses (supply-chain security, incident classification, etc.).
- Document procedures for patching, change control, vulnerability management, and disaster recovery.
Close Cybersecurity & Monitoring Gaps
- Deploy or upgrade endpoint protection, network segmentation, identity & access management with MFA, encryption, and continuous monitoring (SIEM / SOAR).
- Incorporate secure-development standards and “cyber hygiene” training to satisfy NIS2.
- Leverage threat-intelligence feeds to support early detection and timely incident reporting.
Harden Business Continuity & Disaster Recovery
- Identify critical business services (e.g., payments, trading) and set impact tolerances (RTOs/RPOs).
- Provide redundant infrastructure—secondary data centres, multi-cloud fail-over, off-site backups—and test fail-over at least annually.
- Keep recovery procedures and evidence ready for supervisory review.
Build Incident-Response & Reporting Playbooks
- Define detection, escalation, containment, and eradication steps for each incident type.
- Integrate country-specific notification timelines: 24 h (NIS2 initial), 72 h (NIS2/GDPR detailed), and DORA timelines for major ICT events.
- Prepare pre-approved report templates and rehearse end-to-end response scenarios.
Tighten ICT Third-Party Risk Management
- Maintain a real-time register of all critical ICT suppliers; classify each by risk tier.
- Embed contractual clauses on security, audit rights, incident notification, and orderly exit.
- Monitor performance via attestations (ISO 27001, SOC 2) and onsite or remote audits; document contingency and exit strategies.
Train Staff & Foster a Resilience Culture
- Deliver ongoing cyber-awareness and data-protection training tied to real attack scenarios.
- Conduct tabletop and live-fire exercises that involve senior management, simulating ransomware, cloud-outage, or data-exfiltration events.
- Run post-incident reviews and feed lessons learned back into policy and control updates.
Document, Measure, and Audit
- Keep a provable audit trail; policies, risk registers, test results, incident logs, vendor reviews, and board minutes.
- Track key risk indicators such as number of critical incidents, mean time to recover, and third-party risk ratings.
- Use a GRC platform to centralise evidence, streamline supervisory requests, and support continuous improvement.
Stay Current & Collaborate
- Monitor regulatory updates (ESA technical standards, ENISA guidance, national authority circulars).
- Participate in sector information-sharing bodies (e.g., ISACs) to exchange threat intelligence and best practices.
- Adjust controls proactively as new vulnerabilities, attack patterns, or supervisory expectations emerge.
How GRC & RegTech Enable Operational Resilience Compliance
Managing the overlapping demands of DORA, NIS2, GDPR, and Basel III with spreadsheets quickly becomes risky and resource-heavy. Modern GRC (Governance, Risk & Compliance) platforms and other RegTech tools provide the structure, automation, and evidence regulators now expect.
| GRC Capability | How it Supports Digital Operational Resilience & Multi-Regime Compliance |
|---|---|
| Unified control framework | Map one control (e.g., “annual recovery-plan test”) to DORA, NIS2, GDPR, and internal standards at once. Test once, satisfy many mandates, and spot unmapped requirements instantly. |
| Central risk register | Maintain enterprise-wide ICT, operational, and third-party risk records with built-in scoring and links to mitigating controls, which is critical for DORA’s risk-management pillar and Basel capital calculations. |
| Policy lifecycle & evidence vault | Store policies, procedures, test results, and board minutes in a single repository with workflow for review, approval, and employee attestation, making audits and change management simpler. |
| Automated workflows & alerts | Trigger tasks for 24-hour / 72-hour incident notifications, schedule annual penetration tests, and set reminders for quarterly vendor due-diligence, thereby reducing deadline misses. |
| Third-party risk module | Keep a live inventory of ICT providers, contracts, risk scores, and exit strategies; export the DORA-required register of critical suppliers at the click of a button. |
| Incident & issue tracking | Log cyber incidents, outages, and data breaches in one format; link root-cause analyses and corrective actions; analyse trends to drive continuous improvement. |
| Real-time dashboards & reports | Provide heat maps, control-coverage percentages, and “traffic-light” compliance status; generate on-demand DORA or NIS2 reports with evidence links for supervisors. |
| Immutable audit trail | Timestamp every change, risk score edits, policy updates, and incident closures, demonstrating accountability and reinforcing trustworthiness. |
Practical Benefits
- Eliminates duplication: central mapping slashes parallel testing and documentation effort.
- Enhances transparency: executives and regulators see the same live metrics.
- Enables continuous improvement: trend analytics uncover weak spots before they become breaches.
Selecting the Right Platform
Choose a solution that already covers IT risk, third-party risk, business-continuity, and audit, with content packs aligned to DORA and NIS2. Ensure it can evolve as standards change, integrates with SIEM/ITSM tools for automatic incident ingestion, and supports API access for future RegTech extensions.
Advancing Towards Operational Resilience Under DORA, NIS2, GDPR & Basel III
Operational resilience succeeds only when leadership, culture, and controls move in lock-step. Use the checklist below to embed resilience into strategy, governance, technology, and day-to-day operations.
| Priority | What to Do | Why It Matters |
|---|---|---|
| 1 Make resilience a board-level KPI |
• Add operational resilience objectives to the corporate scorecard. • Define tolerable disruption for every critical service before approving budgets or new technologies. |
Aligns investment with impact-tolerance expectations and shows top-down accountability. |
| 2 Stand up a cross-functional resilience team |
• Bring together IT, cyber, risk, compliance, legal, and business owners. • Meet quarterly to track regulatory milestones and incident readiness. |
Breaks silos so reporting, testing, and recovery plans stay synchronised. |
| 3 Drill early, drill often |
• Run full-scale scenarios each year (cyber-attack, cloud blackout, data breach). • Involve executives to rehearse decision-making and communications. |
Turns plans into practical skills and reveals gaps before regulators do. |
| 4 Deepen third-party collaboration |
• Share obligations with critical ICT suppliers and embed audit, drill, and incident-notice clauses. • Invite key vendors to continuity exercises. |
Meets oversight rules and reduces supply-chain single points of failure. |
| 5 Leverage external benchmarks |
• Map programmes against ENISA guidance, Basel principles, ISO 22301/27001. • Commission external audits for independent assurance. |
Provides objective proof that controls follow best practices. |
| 6 Upskill teams continuously |
• Fund regulatory workshops for compliance teams; deliver secure-coding, cloud-security, and IR training. • Encourage certifications (CISM, CISSP, CRISC). |
Reduces human-error risk, a common root cause of incidents. |
| 7 Perfect crisis communications |
• Pre-draft regulator notices, customer emails, press releases, FAQs. • Align timing with statutory deadlines. |
Timely transparency preserves trust and meets legal requirements. |
| 8 Manage by metrics |
• Track uptime, MTTR, unresolved test findings, vendor risk scores, training completion. • Review trends in executive meetings and escalate outliers. |
Demonstrates a live control system rather than a checkbox exercise. |
| 9 Keep a living compliance calendar | • Log all statutory tasks (board reports, national drills, reviews) and set reminders 90/60/30 days ahead. | Prevents deadline slippage and last-minute firefighting. |
| 10 Embed continuous improvement |
• After each incident or drill, run root-cause and lessons-learned reviews. • Refresh controls as new technologies or laws emerge. |
Maintains long-term resilience and future-proofs compliance. |
Reduce your
compliance risks

